The Search for Cyber-Sanity
The Cure: Zero Trust and Holistic Cybersecurity
You have probably had this feeling. Someone comes up with an idea and you think, “Wow, that was obvious, why didn’t I think of that?”
The intention of this article is to create such a moment for you at the start of this new year. The context is cybersecurity. An example I saw recently was a scoring system that addressed 60+ cybersecurity threats and rated cybersecurity by your ability to defend against these vulnerabilities. Get a high score and all is great, right? Although this sounds like a good idea and the actions addressed are entirely valid, they only dealt with about 35% of the organizations’ cybersecurity issues.
This is a symptom that is prevalent across the telecom and IT industries. Most cybersecurity services and products focus on the IT department, touting so-called “complete” branded cybersecurity solutions, yet missing critical actions, leaving many weak links that can impact the entire organization. What’s missing is that all these complete solutions go against the famous defense department expression “your security is as good as your weakest link.”
Enter holistic cybersecurity covering all aspects of your organization, small and large, starting critically with the executive team. It spans all departments (including of course IT). It includes your distributed workforce; all your suppliers outsource companies and contractors. Every departmental function has a critical role to play.
“Zero Trust applies across the organization not just to information technology, with only 32% of actions within IT. The remainder are distributed across the organization: Executive Team 15%, Asset Curation 14%, Operations 10%, HR 8%, etc.”
Just as Zero Trust has become a necessary element of IT, it is also equally relevant across the organization’s ecosystem too—a point not made elsewhere. You may be unaware of Zero Trust or you’ve been presented with “Complete Zero Trust Solutions” without really understanding the actual meaning and relevance. For that reason, the next section of this article sets the record straight. It also helps deal with some new areas not currently addressed in Zero Trust.
This article replaces common misconceptions about cybersecurity with facts and actions that will set you on the path to hype-free “Cyber-Sanity” that encompass holistic cybersecurity and the role of Zero Trust.
What It Is
Zero Trust is a set of principles and strategies not a single solution for IT—don’t be persuaded otherwise. You will have many context-dependent implementations across your organization and ecosystem. The defense deployed depends upon the specific threat and where that threat exists.
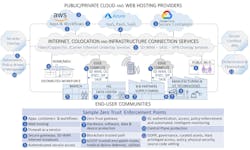
The hybrid cloud with its distributed resources, supply chain and open-source software weaknesses means the network perimeter no longer exists to be defended. (See Figure 1.) While some of you or your clients may be at the early stages of migration to the cloud, many are dealing with myriad challenges: hybrid models of workflows spanning multiple clouds and partners, locally located edge locations, data centers and distributed IT/OT architectures.
Two additional factors are also in play:
- COVID-19 driven distributed workforces are likely to be permanent even if a (mostly) back to the office movement sticks.
- Cryptocurrency has been another enabler of untraceable payment that was never previously available. (Even given the seeming collapse of crypto exchanges, it will remain to be seen how this plays out in the future.)
Exploitation
State-sponsored attacks have extracted billions of dollars. Just a few of these are listed below:
- Phishing/Ransomware-as-a-Service (PhaaS & RaaS)
- Living-off-the-land attacks
- Lateral movement attacks
- Insider and supply chain threats
- Open-source infiltration
- Insecure application program interfaces (APIs)
- Device/hardware exploits
These all prey on the vulnerabilities exposed by the creation of the dynamic ecosystem shown in Figure 1. The cause and exploitation by these threats show why Zero Trust principles and strategies must be applied and embraced by both you and your clients—and why Zero Trust has become and will remain critical.
- Zero Trust Principles are:
o Don’t Trust, Verify.
o Assume breach, meaning the attackers are already inside.
o Least privilege, meaning users, software and devices are only given sufficient authority to
perform a task and for a limited time.
o Prevention of information being exfiltrated or intercepted on exit as opposed to just
preventing access to or overwriting of information.Don’t Trust, Verify.
- Zero Trust Strategies implement the principles by:
o Using identity management and authentication of actors—users, software, devices to
authorize access.
o Implementing actor-specific policies, controls, management, and enforcement that
govern the type of access permitted.
o Automating constant, time-sensitive monitoring to allow scalability and to ensure the
previous points are being followed.
o Automating testing to verify system prevention, operation, and remediation in case there
is an attack.
“Only when you approach cybersecurity holistically does it become blindingly obvious that Zero Trust is both an organizational and technical strategy that should shape your organization.”
Holistic Cybersecurity and Zero Trust
Zero Trust applies across the organization not just to information technology, with only 32% of actions within IT. The remainder are distributed across the organization: Executive Team 15%, Asset Curation 14%, Operations 10%, HR 8%, etc. (See Figure 2.)
It’s essential for cybersecurity to be treated as an imperative by the executive team. (In fact, I really wrote this for those executives who have neither the time nor inclination to hear that hard reality.) If holistic cybersecurity is not understood or adopted by the organization’s leadership, it will likely fail—and your organization will remain at risk. The executive responsible is ideally the chief security officer (CSO). He or she must be the leader of a financially sound security policy and execution strategy and ensure it is constantly monitored by his/her management team.
Implementation
Your HR team must not trust but verify in-house staff (especially including the executive team), distributed workers, contractors, and outside physical security firms. HR must also develop an insider threat strategy that begins with training and a new level of watchfulness based on the premise: Don’t Trust but Verify.
Many activities must necessarily be delegated to outside organizations. It’s all too easy to trust or abdicate responsibility, which is never a defense. These experts could include outside CPAs and legal firms, physical security firms, cloud and network providers, MSPs, etc. Sales software companies and web content management systems have hundreds of outside software elements and are vulnerable. This means that while the professionals of your partners in these areas may be trustworthy, these complex systems are constantly vulnerable to third party attacks.
It's important to cast a wide net that also includes operation technology systems and manufacturing plants. These fall under the same category as third-party systems as they are exposed to attacks. Partners and suppliers needing access to corporate information must be properly managed to verify they are operating sensibly with systems automating their bill of material processes. (The full scope of these actions is just touched upon here but hopefully this is enough to get the point across.)
Cyber-Sanity is Possible!
This article was written to create questions in your mind. The next step is to dive deeper to find the answers you need. Thankfully, there is a resource available for you to tap into. My book on holistic cybersecurity is a playbook with concrete advice, strategies, and step-by-step guidance to simplify the journey to holistic cybersecurity.
Only when you approach cybersecurity holistically does it become blindingly obvious that Zero Trust is both an organizational and technical strategy that should shape your organization.
Where Should Zero Trust Be Deployed?
Information and network technology is clearly central to organizational cybersecurity.
What’s less obvious is where and how Zero Trust should be deployed. The Figure 3 chart below makes it obvious why there is no single solution! Map the diagram onto your organization and decide what matches the assets you need to curate and protect.
Types of Deployment
Deployment of solutions that enforce and implement the strategies may span several locations, over a “Trusted Tunnel or Route” or workflow, or at a single location.
Summary
- A holistic approach to cybersecurity applies across the technical and organizational ecosystem.
- Zero Trust principles are and will remain a critical part of cybersecurity and can also be applied not only in the technical ecosystem but across the organization ecosystem.
- Not every scenario is covered by Zero Trust principles. Specifically, the concept of trusting channel or tunnel between two points or actors is a conversation that is in process. There are challenges ahead in the area of trust and delegation to third party supply chains and partner companies that scale to global and political scenarios.
- Be prepared. This is a topic that changes every day. Great concentration is required.
What’s next?
- Read the latest edition of the book (on Amazon at https://amzn.to/3P7xb1U) Hey Who Left The Back Door Open? – A Holistic Approach To Cybersecurity.
- Visit the web site cybyr.com for the latest cybersecurity news and Top Ten Holistic Cybersecurity actions.
- Contact us at [email protected] for cybersecurity services including an AI-based appraisal of your organization’s holistic cybersecurity posture and to receive a step-by-step playbook to take your organization to safe ground.
If the work enables you to mitigate the most vulnerable threats to your organization’s existence and deflect threats to less prepared targets, then it will have succeeded.
About the Author
Mark Fishburn
Provider of Strategic Network, Cybersecurity, Software, and Marketing Services
Mark is President of cybyr.com and has five decades of experience in software, networking, and security. He is a member of ONUG, Mplify, and CSA network and security working Groups, CISA contributor and publisher of the Holistic Cybersecurity book: Hey Who Left The Back Door Open? For more information, or to give feedback, email [email protected] or follow him on LinkedIn.