Keeping Your Clients’ “Things” Secure
Verizon Recommends the NIST Cybersecurity Framework for IoT Mobile Security
Companies today realize that flexibility is an important part of attracting new talent. What they may overlook is that “flexibility” means more than where people work. It encompasses the type of mobile devices they can use at work. In our recent survey—632 professionals responsible for the buying, managing and security of these devices responded—85% said that the workplace flexibility and what devices employees can use will be important to attracting the best new talent. (See Figure 1.)
When asked how critical, on a 10-point scale, mobile devices were to the smooth running of their organization, 91% of respondents in our survey answered seven or above—78% answered eight or higher. The picture was very similar regardless of company operations (local, regional, or global) or company size (small businesses to enterprise).
“Even worse, the severity of security attacks has grown. Of those that had suffered a mobile-related compromise, 73% described the attack as major, and 42% said that it had lasting repercussions.”
But as working practices have evolved, cybercriminals have been able to adapt, too. In some cases, the increase in remote work has given them a new advantage.
That at least partly explains the “unprecedented increase”, in the words of the Federal Bureau of Investigation (FBI), in cybercrime. Our survey results concur. Almost four-fifths (79%) of respondents agreed that recent changes to working practices had adversely affected their organization’s cybersecurity.
Close to half of the companies that we surveyed said they had suffered a compromise involving a mobile device in the past 12 months. Companies with a global presence were even more likely to have been affected. More than three in five (61%) had been hit, compared to 43% of organizations with only a local presence.
Even worse, the severity of attacks has grown. Nearly half of respondents that experienced a mobile-related compromise said that cloud-based systems/apps were compromised as a consequence. Of those that had suffered a mobile-related compromise, 73% described the attack as major, and 42% said that it had lasting repercussions.
With more respondents saying that their company had experienced a mobile-related compromise, this means more companies are facing major—and lasting—consequences. And despite spending more, chief information security officers (CISOs) are feeling the pain.
Almost four-fifths of respondents agreed that recent changes to working practices had adversely affected their organization’s cybersecurity. And almost two in three CISOs across all regions agreed that remote working makes their organizations more vulnerable to cyberattacks.
According to a recent Proofpoint report (www.proofpoint.com/us), over half of CISOs across all regions agreed that targeted attacks on their organizations have increased since adopting mass hybrid working. Small organizations seem to have been affected most, with 59% of companies with 500 or fewer employees saying that their workforce has been targeted more since they implemented hybrid working. At the other end of the scale, only 48% of large enterprises (5,000 employees and above) said the same.
“Many IoT devices are out in the field. Isolation can also make devices vulnerable to SIM theft, one of the simplest types of attack to carry out—often all that’s required is a screwdriver.”
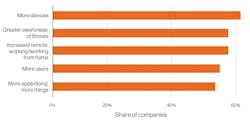
As a result, 77% of MSI respondents said their security spend had increased in the preceding year. More than a fifth said that it had increased significantly. (See Figure 2.)
The Danger of Things
When it comes to the IoT, how can you help your clients keep their “things” secure? To start, it’s important to realize that many clients are lacking central coordination of their IoT projects. Oftentimes, these projects are led by the lines of business and don’t even have to follow standard security requirements.
Remind them that an IoT device can be an attack vector (a weak point that can be exploited to mount an attack), a vehicle for attacks (like a part of a botnet used to carry out a distributed denial-of-service (DDoS) attack), or a target in its own right. Share how the nature of IoT devices themselves also present distinct challenges compared to securing other mobile devices. These fall into these categories:
- Variety: The sheer volume and diversity of IoT devices can present enormous logistical obstacles to effective device security. It doesn’t help that many IoT products have been found to have extremely weak cybersecurity—including security devices such as smart locks, doorbells and, ironically, security cameras.
- Distance: Many IoT devices are out in the field. This can make them vulnerable to physical tampering or network attack and harder to update or replace. Isolation can also make devices vulnerable to SIM theft, one of the simplest types of attack to carry out—often all that’s required is a screwdriver. All the hacker has to do is break open the connected device, such as a smart lamppost, and remove the SIM. This can then be put into another device, giving the user free calls and data at the organization’s expense.
- Longevity: In the survey for the previous edition of this report, we found that over half (54%) said that some of their IoT devices had an anticipated lifetime of five years or more—up from 36% in our previous report. This would be very old for a smartphone or laptop. Combined with the difficulty of updating devices, this can make it hard to keep IoT protected against constantly evolving threats.
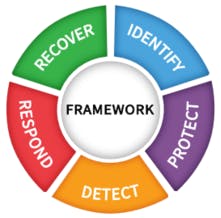
Recommend your clients proactively adopt five functions from the NIST Cybersecurity Framework. (See Figure 3.)
“When it comes to the IoT, how can you help your clients keep their ‘things’ secure? To start, it’s important to realize that many clients are lacking central coordination of their IoT projects. Oftentimes, these projects are led by the lines of business and don’t even have to follow standard security requirements.”
Identify
- Thoroughly review the security before you purchase anything.
- Ask potential vendors to supply details of their security measures and review them for robustness.
Protect
- Harden all devices, including ensuring they are tamper-resistant and tamper-evident.
- Change all default or vendor-supplied passwords.
- Change all default or vendor-supplied passwords, really.
- Shut down anything you don’t need—if you’re not using a port or protocol, block it.
- Keep devices patched—use over-the-air (OTA) updates to help keep devices secure, especially those in remote or difficult-to-access locations.
- Bind SIMs to devices, limiting the potential damage of SIM theft.
- Use private, non-routable IP addresses to make it harder for attackers to access IoT devices.
- Consider using a private cellular network to keep devices off the public Internet.
- Encrypt data in transit and at rest.
- Create an IoT security assurance process that regularly analyzes IoT risk in your organization that users developing or purchasing IoT programs work with the information security team to factor in the cost and resources required to secure devices and applications.
Detect
- Use network intrusion detection tools to monitor all traffic, incoming and outgoing, for unusual activity and put in place a process to handle any alerts promptly.
- Subscribe to a threat intelligence service to get early warning of emerging threats.
- Analyze logs for signs of suspicious behavior.
- Integrate MTD with EDR or security incident event management (SIEM) to help simplify monitoring and, should it be necessary, forensic analysis.
Respond
- Put controls in place to contain the spread of infection and prevent the attacker from gaining any additional access or access to sensitive data.
- Implement network blocks to limit an attack from infecting more devices or the attacker from accessing more critical systems.
Recover
- Conduct a postmortem to determine how the attack managed to get through and where controls, processes and technology fell short, and then distribute an “after action” report.
This article is adapted from Verizon’s Mobile Security Index 2022. For more information, please visit: https://www.verizon.com/business/resources/reports/mobile-security-index/
Verizon Social Media Links
Facebook: https://www.facebook.com/verizon
Twitter: https://twitter.com/verizonbusiness/
LinkedIn: https://www.linkedin.com/company/verizonbusiness/