Cloud Tech Increases Insider Risk
Exponential growth, lagging indicators, flattening the curve—the pandemic forced us all to get familiar with concepts like these. And these same ideas are extremely relevant to how we should all be thinking about Insider Risk. Almost every company today is dealing with it. But awareness of the problem is a “lagging indicator” of what’s really going on inside most organizations.
Almost all companies (96%) identify the need to improve the data security training they give to employees, with around a third (32%) saying they need a complete overhaul.
The proliferation of cloud tech keeps accelerating Insider Risk—amplified by the not-going-away-anytime-soon Great Resignation and the here-to-stay shift to hybrid-remote work models. Cybersecurity practitioners are sounding the alarm bells on exponentially growing Insider Risk. Yet when it comes to Insider Risk mitigation, budgets aren’t shifting to compensate, and most companies haven’t prioritized improving their Insider Risk Management (IRM) capabilities. Awareness without action is leaving a huge gap: 71% of companies still don’t know what and how much sensitive data is moving outside corporate visibility—or walking out the door with departing employees.
The Numbers You Need to Know
Vanson Bourne recently conducted a surveyed of 700 business leaders, security leaders, and practitioners from companies in the US to take the pulse of the cybersecurity data protection challenges.1 The data says it all: 96% of companies experience challenges protecting corporate data from Insider Risks and 73% report it’s a big problem within their company.
If you think that only applies to your customers, think again. Telecom providers are not immune. In fact, there is a one in three (37%) chance your company loses IP when an employee quits. And 71% of respondents are concerned about their lack of visibility over what and how much sensitive data departing employees take to other companies. Still, only 21% of companies’ cybersecurity budgets have a dedicated component to mitigate this problem.
But the numbers only tell part of the story here. Digging into the challenges our survey respondents reported, three key trends are clearly driving rising Insider Risk in almost every organization:
- Cloud Technologies Drive the Modern Workforce: The sprawling adoption of cloud technologies by the hybrid-remote workforce and security’s lack of visibility into data as it moves across those technologies.
- The Great Resignation: Sustained, high turnover increasing risk of departing employees’ theft of IP.
- Internal Misalignment on Insider Risk: Ongoing misunderstanding and poor communication between stakeholders at the board, security leadership, and security practitioner levels.
The accelerating cloud shift got turbocharged by the pandemic and today’s modern hybrid-remote workforce. But these cloud super-tools have their own kryptonite: The same capabilities that empower employees to connect, create and collaborate faster and easier also make it faster and easier to exfiltrate data (intentionally or unintentionally).
The problem here isn’t just that employees are exfiltrating files via cloud apps. It’s that cloud visibility is a huge blind spot for most security teams. This is especially true for files moved to an untrusted or unauthorized location (i.e., not within the corporate cloud environment) or for companies using outdated data protection tools like DLP that can’t see cloud activity because they were built for an age before the cloud.
These fears are at risk of becoming reality as eight in ten (80%) report that reputation has/would be impacted because of an Insider Risk event involving loss or theft of sensitive information. These impacts should serve as significant motivators for those without an IRM program to implement one.
The 2022 Data Exposure Report survey reflects these realities: 71% of cybersecurity professionals are concerned about sensitive data hosted outside of corporate storage where security teams lack visibility.
There seems to be a culture of disconnect around the problem, which leads to uncertainty around ownership.2 Insider Risk is simply not being talked about enough from the top down or the bottom up. In addition, companies need a better understanding of data movement. They don’t just need more visibility, they need better, more contextual visibility to determine what data movement poses unacceptable risk to the business. Lastly, employees are simply unaware of the risks they pose to the company. Despite resources and technology and training, employee security awareness remains a challenge.
Budget and Programs
Even so, only 21% of companies’ cybersecurity budgets are currently dedicated to mitigating Insider Risk, on average. In 2021, 54% of cybersecurity leaders spent less than 20% of their budgets on this.
Thankfully, the acceptance of the need to increase the budget is increasing, with 73% of respondents stating that their companies’ budget for protecting against Insider Risk is insufficient. There is positive momentum because 61% of companies are currently using a program specifically devoted to this type of data management and 36% are planning to implement one in the future.
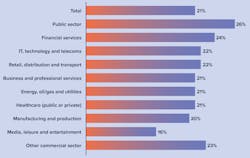
When reviewing responses by industry, public sector and financial services companies are leading the way in IRM and protecting valuable data, based on the percentage of their global cybersecurity budget dedicated to mitigating the problem. (See Figure 1.)
Read on to learn how insider risk can hurt your company’s reputation and why employees are your most effective first line of defense.
Bad Rep?
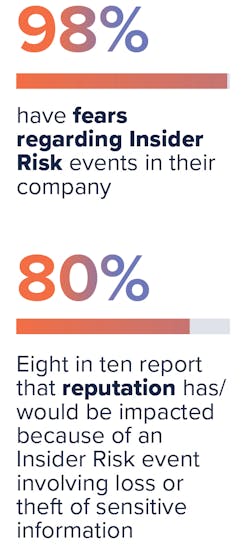
Concerningly, 98% of respondents have fears regarding Insider Risk events in their company, with reputational damage, loss of IP/customer data and revenue loss being the three most likely concerns.
These fears are at risk of becoming reality as eight in ten (80%) report that reputation has/would be impacted because of an Insider Risk event involving loss or theft of sensitive information. These impacts should serve as significant motivators for those without an IRM program to implement one. (See Figure 2.)
An Overlooked Opportunity
Interestingly, survey responses showed that most companies could make major headway against this problem with one simple, tactical strategy: better, smarter employee training.
Unfortunately, rigid tech solutions (i.e., DLP, CASB) just don’t work because they can’t account for human ingenuity/creativity, and ultimately drive Insider Risk further into the shadows. This has never been more apparent: As companies continue adapting to new ways of working and hybrid-remote models, over half (55%) of respondents say they’re worried employees have become lax in their cybersecurity practices/protocols.
Almost all companies (96%) identify the need to improve the data security training they give to employees, with around a third (32%) saying they need a complete overhaul.
Unlike other data security challenges, the unique part about Insider Risk is you can get the threat factors working with you. But the key is evolving cybersecurity awareness and training to reflect the new ways of working.
That’s why we have created Incydr. We are committed to giving companies a clear signal of their biggest data risks and empower them with information to take action faster.
RESOURCES AND NOTES
1. 2022 Data Exposure Report: https://www.code42.com/resources/reports/2022-data-exposure
Code42 commissioned independent market research agency Vanson Bourne to conduct the Data Exposure Research. The 2022 study surveyed 700 respondents (150 senior business leaders, 200 senior cybersecurity leaders, and 350 cybersecurity practitioners) from companies in the US in September and October 2021.
2. The Disconnect Between Cybersecurity Practitioners and Business Leaders: https://www.code42.com/blog/the-disconnect-between-cybersecurity-practitioners-and-business-leaders/
ABOUT THE AUTHOR
Mark Wojtasiak is VP of Portfolio & Product Marketing, Code42. He leads the market research, competitive intelligence, and product marketing teams. Mark joined Code42 in 2016 bringing more than 20 years of B2B data storage, cloud and data security experience with him, including several roles in marketing and product management at Seagate. For more information, please visit www.code42.com. You can also follow Mark on Twitter @markwojtasiak and Code42 on Twitter @code42.
About the Author
Mark Wojtasiak
Vice President of Portfolio & Product Marketing, Code42
Mark Wojtasiak is VP of Portfolio & Product Marketing, Code42. He leads the market research, competitive intelligence, and product marketing teams. Mark joined Code42 in 2016 bringing more than 20 years of B2B data storage, cloud and data security experience with him, including several roles in marketing and product management at Seagate. For more information, please visit www.code42.com. You can also follow Mark on Twitter @markwojtasiak and Code42 on Twitter @code42.