Streamlining Identity Verification Is Part of a Proactive Approach
Over the past decade, the telecommunications industry has successfully incorporated vast arrays of exciting, cutting-edge technology—such as 5G, cloud computing, artificial intelligence, virtualization, and the Internet of Things (IoT). However, there are ways in which the industry has lagged technologically, leaving them vulnerable when it comes to regulatory compliance, fraud prevention, customer data protection, and providing a better customer experience. Identity verification practices and regulatory compliance processes have failed to catch up to these other advancements. Overhauling outdated practices can benefit all parties involved—organizations, customers, and regulators alike.
“Account takeovers cost companies a total of $1.62 billion in the last reported year, according to a 2021 Communications Fraud Control Association report (CFCA).”
The sophistication of fraud and methods to commit financial crime grows every day. “Telco fraud” specifically can be committed when there are weak processes in place to verify a customer’s identity. For example, subscription fraud, where fraudsters open accounts and commit to a contract using stolen identity documents and banking information. Other key types of fraud committed by third parties against telecommunications companies include account takeovers via online user accounts, where a fraudster gains access to the account login details, signs in, and now controls access. Account takeovers cost companies a total of $1.62 billion in the last reported year, according to a 2021 Communications Fraud Control Association report (CFCA). International Revenue Sharing Fraud (IRSF) is when a corporate phone system is hacked to call premium-rate phone numbers that the fraudsters own, and they are earning money off every call made. SIM Swapping is often reported on by mainstream media and it occurs when a fraudster highjacks a person’s SIM card to contact their service provider and request a transfer of the service to a number they control. These fraudulent actors can then intercept Two Factor Authentication via SMS or OTP (one-time passwords) sent to the phone from the victim’s social media accounts or banking provider.
Fraud doesn’t just cut into margins; it creates a vicious cycle when it comes to regulatory compliance—companies with lax fraud prevention will be subject to fines by regulators. Britain is setting the new standard for fraud prevention legislation by not just punishing companies who commit fraud, but also the companies who don’t properly prevent it. The Economic Crime and Corporate Transparency Bill, currently in the process of being passed, allows companies to receive unlimited fines even if they were unaware of any fraudulent activity occurring within their organization. British lawmakers have proposed this legislation to “discourage organizations from turning a blind eye to fraud by employees which may benefit them”.
One of the cornerstones of telecommunications fraud prevention legislation in America is the Truth in Caller ID act. This piece of legislature prohibits the use of caller ID spoofing with the intent to defraud, cause harm, or wrongfully obtain anything of value. It also requires the FCC to prescribe regulations to protect consumers from misleading or inaccurate caller ID information. In 2016, several telecommunications companies tied to Adrian Abramovich made nearly 100 million robocalls over a three-month period in 2016. The calls were made to consumers in all 50 states and were spoofed to appear as if they were coming from local numbers. When the recipient answered the phone, the salesman would use misleading and high-pressure sales tactics to push vacation time-shares. After an investigation, the FCC issued a $120 million fine against Abramovich and his companies, which was at the time the largest fine in FCC history for illegal robocalling. The FCC found that the calls were made with the intent to defraud or cause harm, and that the company had deliberately used false caller ID information to evade call-blocking technologies and increase the likelihood that consumers would answer the calls.
How could modern technology have prevented this fraudulent activity and ensuing lawsuit? Caller ID verification technology has become increasingly sophisticated over the past several years, with some systems able to use machine learning and artificial intelligence to analyze call patterns and identify potentially fraudulent activity. In Britain, thanks to collaboration between banks and the telecom sector, there are new data sharing exercises to detect these types of phone calls, currently being rolled out across all mobile networks. Some British banks are also profiling the risks associated with a call, by combining network authentication, audio modulation and AI technologies. If a call is flagged to be from an abnormal environment, this can be investigated to see if fraud is being attempted. Such a system could have easily flagged the calls made by Abramovich’s company by accurately pinpointing the location of the calls and confirmed it was incongruous with the caller’s claim that it came from a local number.
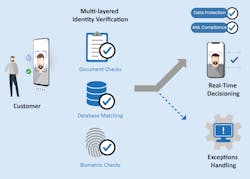
While the telecommunications industry may encompass a very broad umbrella of very different industries—mobile phone networks, traditional landline phone networks, satellite communications, cloud communications, and telecommunications software—these diverse sectors are united in their need for modern fraud prevention tactics, mainly via identity verification. Mobile phone network providers can benefit from digital identity verification because their practice often faces scrutiny from KYC regulations.
To prevent money laundering, terrorism financing, and other illegal activities mobile phone network providers are required to collect a government-issued ID or passport from customers. Biometric technologies like liveness testing and facial matching are a faster alternative to traditional onboarding methods as they enable customers to verify their identities instantly. There are other strong walls of defense against fraud including:
- Document verification to ensure what’s submitted for identity verification purposes has not been forged or tampered.
- Address verification—where the individual’s name and address are extracted from the onboarding information
Identity verification solutions can be integrated to both physical store and online journeys, thus offering customers a secure, friction-free experience in-person or remotely. Modernizing identity verification further benefits the telecommunications industry by eliminating manual identity verification and account creation, which can be prone to human error.
By making the identity verification process smooth, efficient, and secure, the telecommunications industry can take a significant step towards preventing fraud at the source. By incorporating cutting-edge technology, organizations can save labor and capital and protect their businesses from financial losses and reputational damage, while also ushering in a new era of security and trust between their business and customers. Customer satisfaction and brand loyalty can be greatly increased if users are shown their personal data is being processed to the highest of safety and compliance standards.
About the Author
Colum Lyons
CEO, ID-Pal
Colum Lyons is the CEO of ID-Pal, an off-the-shelf identity verification solution that verifies an identity in real time using biometric, document and database checks. Colum founded ID-Pal in 2016 after seeing the need for an easy, streamlined, secure digital AML and KYC compliance process. For more information, please email [email protected] or visit https://www.id-pal.com/. Follow Colum on Twitter @ColumLyons and LinkedIn: https://www.linkedin.com/in/columlyons/?originalSubdomain=ie. Follow ID-Pal on Twitter @TweetIDPal and LinkedIn: https://www.linkedin.com/company/id-pal/?originalSubdomain=ie.