A New Approach to C*********ity
Key Highlights
- Security should be positioned as a business enabler, not a cost center or fear-driven obligation.
- Create a Holistic Resilience and Security Policy covering the scope of actions and the goals measuring the impact on the organization. Complement it with a Plan of Action outlining short-term, achievable steps across all departments.
- Switch the conversion from avoiding risk to strengthening the organization.
New Thinking to Enable a Stronger Organization
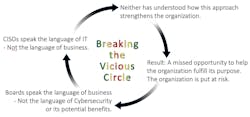
Let’s face it, droning on about impending doom to the organization: “if we don’t deploy resources (money and staff) to reduce our security risks now, then I can’t be held responsible …” goes down like a lead balloon. Whatever you say next is not listened to. Instead, the executive minds return to dealing with other issues or how to execute the next big plan. You will notice that even the title of this article couldn’t bring itself to use the word cybersecurity!
It’s time to change that with an approach that will open closed minds. After authoring the article on Resilience in the fall edition, I had one of those “why didn’t I think of this before?” moments, realizing that it was all in the language and the impact on the listener. It’s switching from the part of the brain that reacts to an amygdala attack to fostering being inspired by new possibilities.
This article is not about brain science; it’s about:
- Putting all actions in the context of strengthening the organization by changing the mindset to enable new possibilities.
- Creating a structure for low-cost execution with a holistic strategy and incremental actions.
- Executing actions related to avoidance, prevention, detection, and removal of disruptions to the goals. Measuring and reporting improvement over time. Then, adapting to the evolving organization and changes that impact the goals for the next iteration.
It’s time to change that with an approach that will open closed minds.
Developing the Executive Language
This begins by using words like “strengthening the organization” and avoiding negative words such as “risk” and “threat avoidance.” I just read a guidance document that used the word “risk” 160 times, along with “vulnerabilities,” insider terms like “security posture,” and acronyms that interrupt the listener’s understanding. Look to see how well-documented resilience and security procedures support sales to differentiate from competitors, remove supply chain fears, etc. Just like privacy policies that no one reads, the security policy should be posted to identify the organization as a modern, powerful company. The same applies to obtaining insurance at lower rates, meeting legal and SEC requirements, and defending its reputation if supply chain vendors cause problems.
Lastly, specifically for ISE Magazine readership, although the focus here is on end-users, there are two difference-making services that could be unique client offerings for service providers. Offering the security services covered in my Assume Breach article (ISE spring edition and cybyr.com/assumebreach) means end-users can both potentially eliminate ransomware and save money by delegating responsibility and costs to service providers. This is exactly the kind of thinking that changes executive mindsets. (See Figure 1.)
Due to limited space, we can only provide the highlights of the approach here. It’s expanded on my website (cybyr.com/strengthening). The idea is to use the work to develop your own powerful, resilient organization (external cost = 0).
Creating a Holistic Strategy and Incremental Plan
To deliver on the promise, two documents are required:
- A Holistic Resilience and Security Policy covering the scope of actions and the goals measuring the impact on the organization. Holistic here means every department and line of business, collaboration with all supply chains, including outsourcing, evolving over time.
- The Plan of Action. This lists short-term actions to be undertaken by each department under your guidance. The execution of the plan will be either action completion or achieving measurable milestones. Its scope includes sales and marketing actions, legal, conformance and compliance, HR, etc., that strengthens the organization. The point is, of course, not to get overwhelmed by too many tasks at once and to observe measurable progress.
Much of this work will consist of interrogation of the organization’s departments to discover vulnerabilities and make agreed recommendations. This is one of the reasons that I wrote Cybyr-AI, my Expert Proactive AI Software to personalize and automate the process, make recommendations, and measure results. However, you may choose to do this yourself (external cost = 0) or with help from a consultant (like me!).
The point is, of course, not to get overwhelmed by too many tasks at once and to observe measurable progress.
Executing the Actions in the Plan
This section breaks down the main tasks related to avoidance, prevention, detection, and removal of disruptions to the goals.
Avoidance and Prevention
Here are some basic actions to take and not to take.
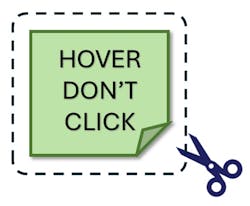
Phishing is easily the #1 source of attacks. There are at least 10 types. However, don’t waste resources on anti-phishing training courses. Recent studies from MIT, etc., show that training is 95% ineffective/useless. Here’s my cut-out and avoidance “device” to stick on your monitor or screen (cost = 0).
You likely know all these, but maybe you don’t: Zero access to corporate networks from unapproved devices. Approved devices must be automatically updated, containing approved software. User authentication (low cost) must only permit access at approved times for approved transactions from approved locations. Executives—that means you too.
Always use passkeys or multi-factor log ins to approved applications. Never reuse an ID/ password or allow people to log in with Google or Facebook identities. If you do, and one site is compromised, as thousands have, then every one of your sites is compromised (cost = 0).
In terms of protection of assets to avoid ransomware, I covered this in the spring issue (“Assume Breach”). The “Resilience” article (fall edition) covered asset protection and the automation of asset updates in detail.
Detection and Removal
The good news is that there are several low-cost options available. For users of Microsoft Office, the email phishing detection is constantly being updated. Anti-malware software from Microsoft Defender, McAfee, MalwareBytes, etc., is likely already in place. (Cost/user relatively small.)
Software Tsunami Warning
I cover around one hundred types of security software and packaged solutions on my cybyr.com/cyberpedia page. The actual number of security products is in the 6-10,000 range! However, the only type of software I think is beneficial for the end-user is Endpoint Detection and Removal software. More on this on my website.
Ongoing Measurement, Reporting and Adaptation
In terms of measuring progress, this is where I have spent much time on software that both measures your status, prioritizes recommendations on next actions and tracks improvements.
Finally, as each cycle of execution completes, it’s time to adapt to developments in the organization and prevailing circumstances, ready for the next cycle.
Summary
I hope this structured approach gives you some inspiration for a more engaged organization at limited external expense. Yes, cybersecurity is critical but the overarching context is the strength of the organization. I hope that you will visit my website and see that many of the steps have been automated to accelerate the adoption of this approach: cybyr.com/strengthening.
Stay Connected with ISE Magazine
Subscribe to our newsletters and magazine for the latest telecom insights, explore the current issue for in-depth features and strategies, and register for upcoming webinars to learn directly from industry leaders.
About the Author
Mark Fishburn
Provider of Strategic Network, Cybersecurity, Software, and Marketing Services
Mark is President of cybyr.com and has five decades of experience in software, networking, and security. He is a member of ONUG, Mplify, and CSA network and security working Groups, CISA contributor and publisher of the Holistic Cybersecurity book: Hey Who Left The Back Door Open? For more information, or to give feedback, email [email protected] or follow him on LinkedIn.