Network Security Tenets for the Long-Term
Communications service providers (CSPs) are starting to realize the potential of 5G by enabling new innovative services. However, such potential will not be realized without building and maintaining a secure 5G network. Mass deployment of 5G networks is well underway, but the work to ensure these networks are secure is ongoing.
Given the recent cyberattacks on non-mobile networks in the United States, from the SolarWinds breach to the pipeline ransomware attack to the Kaseya ransomware attack, security of critical infrastructure including information and communications technology (ICT) networks is front and center.
Security is a critical component of 5G architecture for Standards Development Organizations (SDOs), industry forums, vendors of network functions, and Mobile Network Operators (MNOs). Focus on security threats and controls will continue to be necessary to gain the trust of enterprises, manufacturing, critical infrastructure providers, and governments that are exploring opportunities to leverage 5G for improved communications, operations, and new revenue streams.
This short article is excerpted from a white paper detailing many evolving 5G security considerations. The goal of this article is to take one aspect—zero-trust architecture—and provide a high-level view of the topic so CSPs can address it during their network security journey. The authors aim to promote better security practices in which an organization’s security posture is periodically reassessed to address changes in risk from evolving threats, attack vectors, risk tolerance, and security control technologies.
Zero-trust is a security model built on the principle that no user or network function can be trusted, whether internal or external to the network. Zero-trust shifts the focus away from network perimeter security, instead restricting access by internal and external users and software components through use of strong authentication and least privilege authorization.
Zero Trust Architecture (ZTA)
Traditional networks are based on defined perimeters, where most mobile packet core functions are centralized. The evolving mobile packet core architectures create software-defined perimeters. The 5G RAN and Core may be based on a cloud-native architecture which allows 5G CNFs to be deployed as microservices in the MNO’s private data center or in a public cloud. Multiple vendors will supply NFV Infrastructure (NFVI) components, VNFs, and CNFs for which there will be contractors and sub-contractors requiring access to the 5G network for support, configuration, and deployment purposes.
Perimeter security assumes that the network inside the perimeter is secure and users who have gained access to network functions and data inside that perimeter can be trusted. Perimeter security does not fully protect against threats from supply chain, internal threats, and malware infection supporting lateral movement. The SolarWinds and Kaseya supply chain attacks, and other recent attacks that exploit the perimeter security approach, are driving implementation of perimeter-less security based upon a ZTA, in which there is no implicit trust granted to assets or users based on physical or network location, or ownership.
Zero-trust is a security model built on the principle that no user or network function can be trusted, whether internal or external to the network. Zero-trust shifts the focus away from network perimeter security, instead restricting access by internal and external users and software components through use of strong authentication and least privilege authorization.
As defined by the National Institute of Standards and Technology (NIST), zero-trust focuses on protecting resources, including assets, services, workflows, and accounts instead of protecting network segments. ZTA is built upon the principles of zero-trust to minimize access to resources, such as data, compute resources, applications, and services, to only those subjects and assets identified as needing access, as well as continually authenticating and authorizing the identity and security posture of each access request.
MNOs had designated certain devices, applications, and users as “trusted” and then allowed them broad access to other parts of the network. Threat actors could exploit this, which drives the need for new requirements to provide a robust ZTA for 5G networks. Zero-trust capabilities are inherently available, by standard, in 5G to mitigate security risks. In fact, 5G Americas 3GPP Release 15 and 16 standards for 5G define relevant network security features supporting a zero-trust approach that, if used, could enable MNOs to implement varied deployments of NIST (SP) 800-207 ZTA based on the operator’s network deployment options. (See Figure 1.)
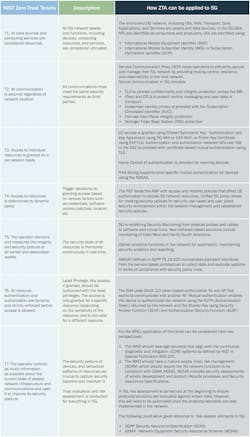
Clearly, 5G networks, which contain cloud-based assets, along with an increasing number of users, devices, and machines, could benefit from zero-trust initiatives. Zero-trust is not a “rip and replace” model. Instead, a ZTA can augment existing architecture using three logical elements as illustrated in Figure 2. The Policy Engine (PE) and Policy Administrator (PA) together form the Policy Decision Point (PDP) that makes decisions enforced by the Policy Enforcement Point (PEP).
Zero-Trust can be applied in different ways and adapted for various systems, including 5G. 5G ZTA is end-to-end including RAN, Transport, and Core, and consists of multiple layers of security to establish trust in user identity, enhanced end-to-end visibility, and trustworthiness of each user device accessing the Data Control Network (DCN) using any cloud deployment model. Figure 3 summarizes the applicability of NIST’s seven tenets of a ZTA to 5G networks.
The SolarWinds and Kaseya supply chain attacks, and other recent attacks that exploit the perimeter security approach, are driving implementation of perimeter-less security based upon a ZTA, in which there is no implicit trust granted to assets or users based on physical or network location, or ownership.
The combination of greater risk with reduced risk tolerance requires a zero-trust approach. 3GPP has introduced an evolution of the trust model for stand-alone 5G deployments, for which trust within the network is considered to decrease as one moves further from the core. Trust in 5G can be enhanced using a ZTA, which makes no implicit assumptions of trust based upon an asset’s network location, geographic location, or ownership.
5G operators will benefit from deploying zero-trust security controls to protect network assets and data and enhanced ability to detect attacks. Those diligent security efforts will allow 5G to deliver on its promises to society and business.
RESOURCES AND NOTES:- NIST SP 800-207 Zero Trust Architecture, https://www.nist.gov/news-events/news/2020/08/zero-trust-architecture-nist-publishes-sp-800-207
- Zero trust and 5G – Realizing zero trust in networks, Olsson. J., et al, Ericsson Technology Review, Ericsson, May 12, 2021, https://www.ericsson.com/en/reports-and-papers/ericsson-technology-review/articles/zero-trust-and-5g
About the Author: Chris Pearson is President of 5G Americas, responsible for the overall planning of the organization, and providing management for the integration of strategy and operations in the areas of technology, marketing, public relations, and regulatory affairs. With 33+ years of experience in the telecommunications industry, he is a recognized spokesperson in mobile wireless and 5G technology trends, and has spoken at technology conferences throughout the world, including CES, Mobile World Congress, CTIA, 5G World North America, and The Big 5G Event. For more information, email [email protected] or visit https://www.5gamericas.org/. Follow 5G Americas on Twitter @5GAmericas.
About the Author