Emerging Cybersecurity Threats in the ICT Industry Need AI Solutions —
The Internet of Things Cybersecurity Improvement Act of 2019 is being introduced in the Senate by Senator Warner, Mark R. [D-VA] (Introduced 03/11/2019). Among other areas, the Act is intended to address IoT device security relative to Secure Development, Identity management, Patching, and Configuration Management. Quoting opinions from market leaders (such as Cloudflare, Symantec, VMWare, and others), the bill asserts a desperate need for cybersecurity regulation.
At the network services provider level, the cybersecurity market is heating up as carriers realize that network advances will increase network complexity, which will translate into increasingly more potential vulnerability areas. Accordingly, communication service providers are both working unilaterally as well as banding together to address common cybersecurity concern areas. By way of example, AT&T recently became the first North American carrier to join the Global Telco Security Alliance, which launched last year with founding members Etisalat, SingTel, Softbank, and Telefonica.
Enterprise and government spending for cybersecurity products, managed services, and professional services, will be substantial over the course of the next few years. Cumulative global spending on cybersecurity products and services will exceed 1 trillion US dollars over the next 5 years with multiple trillions of dollars in cybercrime damages realized through 2024. Accordingly, Mind Commerce sees damage control and mitigation solutions as a critical portion of the cybersecurity market.
At the macro level, spending is driven by the realization of increasingly more voluminous and sophisticated global threats to digital infrastructure. At the business level, company reliance upon the Internet, open interfaces and communication between customers and other companies necessitates robust cybersecurity solutions. In addition, new technologies and solutions such as the Internet of Things (IoT) will require new approaches to cybersecurity and hence innovative solutions.
AI and 5G Networks
In addition to much greater capacity and substantially lower latency, 5G networks are poised to become much more intelligent. In combination with Software-Defined Networking (SDN) and advanced analytics, AI is ready to take autonomous, intelligent network operation and control to an entirely new level.
For example, leading telecom infrastructure provider, Ericsson, claims that their AI-powered RAN enables up to 25% more 5G coverage with advanced traffic management.
InvisiLight® Solution for Deploying Fiber
April 2, 2022Go to Market Faster. Speed up Network Deployment
April 2, 2022Episode 10: Fiber Optic Closure Specs Explained…
April 1, 2022Food for Thought from Our 2022 ICT Visionaries
April 1, 2022While AI has not yet made extensive inroads into the realm of networks, cellular systems in particular will soon achieve early and extensive success through the combination of Machine Learning, SDN, and advanced data analytics technologies.
The potential economic and social benefits cannot be overstated as networks will achieve an entirely new level of self-awareness, self-configuration, self-optimization, self-healing, and self-protection. This will be a benefit for existing networks as well as evolved LTE, emerging IoT systems, and soon-to-be-launched 5G networks.
An interdisciplinary approach will be required for systems integration as many technologies are brought together including Machine Learning, SDN, Network Function Virtualization (NFV), Network Slicing, Quality of Service Management, and advanced security methodologies. Mind Commerce anticipates the total global AI driven networking solution market will reach $5.8 billion by 2023.
It is good that AI will be integral with 5G, because the fifth generation of cellular communications also brings with it security concerns. With improved network capacity, 5G is expected to impose new security challenges across infrastructure, IoT devices, communication network, user identity, and data privacy.
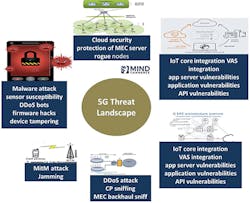
During our analysis of the 5G cybersecurity threat landscape, Mind Commerce identified some common concerns for 5G systems, including intrusion detection and prevention, malware protection, detection of anomalies, malicious protection, radio interface security, roaming security, and DoS attack. One of the biggest 5G security issues at the application layer is the many apps and services supported. (See Figure 1.)
Figure 1. 5G Threat Landscape
With substantially greater bandwidth, and ultra-low latency, 5G supports many new and improved apps and services such as untethered Virtual Reality (VR) and anytime, anywhere telepresence. Whether it is new immersive technologies, or extension of existing apps such as Voice over 5G, there are some common security issues (such as data privacy) and some completely different issues, such as virtual identity theft in VR. (See Figure 2.)
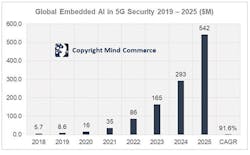
Figure 2. Global Embedded AI in 5G Security 2019-2025 ($M)
With these new threats, there will be an increasing need for embedded AI algorithms within 5G networks. Accordingly, Mind Commerce sees a rapid growth opportunity in this area. Global embedded AI in 5G security (networks, devices, platforms, etc.) is anticipated to exceed $500M by 2025.
One of the moderating factors of this projection is carrier commitment to 5G specific security. By way of example, a recent TF Forum survey indicated that 35% of the 54 communication service provider responding indicated that they do not have a roadmap to extend coverage in the next year. This is despite published results from a recent security audit indicating systemic 4G network vulnerabilities, which is troubling as LTE will remain viable as a complement to 5G.
AI to Protect IoT Networks and Data
Like any network, IoT systems will be subject to intrusion, denial of service, and malware. Communications service providers will need to ensure data privacy and security as well as resource protection.
Carriers will have a certain degree of liability when it comes to the implications for how IoT networks are used by enterprises. One of the major concerns is illegal capture and trade of IoT data which includes users’ activities and records such as personal health, financial information, location, and asset information such as personal vehicles.
Many IoT functions cause actions to be made in an autonomous fashion. If malware or erroneous information (such as control commands) causing harmful actions to take place (such as turning a vehicle off while it is traveling at highway speeds), carriers will suffer public bad-will, to say the least. AI will be an important tool for both carriers and enterprise to safeguard assets, reduce fraud, and support analytics and automated decision-making.
Many existing business processes will be automated via IoT integration as well as new ones developed as a result of new capabilities. Autonomous decision-making has both opportunities and concerns. The use of AI will be critically important to ensure that automated decision-making does not go awry. Mind Commerce has espoused the need for an AI "watcher" function to ensure that embedded AI in silo solutions and/or isolated systems do not make decisions in that are potentially adverse to a given enterprise.
Longer term, AI will move beyond fraud prevention and prevention of malicious acts, as AI will be used to feed advanced analytics and decision-making. This will be especially true in IoT solutions involving real-time data as AI will be used to make determinations for autonomous actions.
AI will play a key role in identifying more than malware and intrusion attempts for IoT. This is because IoT is increasingly comprised of interconnected IoT systems that have the potential for cascading problems should a cyberthreat get out of control. Accordingly, Mind Commerce sees AI as both a front-line point-of-attack defense, for predicting potential offending entities, and a back-line defender of networks, devices, and data, that is indirectly involved due to interconnectivity, data exchange, and command and control directives.
Mind Commerce also sees AI working hand-in-hand with blockchain technology to protect IoT network infrastructure, devices, and data. The 2 technologies complement one another in support of critical Authentication, Authorization, and Accounting (AAA) functions for telecom networks as well as enterprise, industrial, and government systems.
AI in Edge Networks
There are many good reasons to extend computational capabilities to the edge of networks. The cellular carriers are continuously seeking improved data efficiency and the ability to deliver capacity on-demand when and where it is needed. With edge computing, network operators can provide both communications and computational capacity in a much more flexible manner.
The European Telecommunications Standard Institute (ETSI), the prime facilitator of edge computing standardization, has identified a technical framework for Multi-access Edge Computing (MEC). Previously known as "Mobile Edge Computing", ETSI restated MEC to include the term "Multi-access" to recognize that edge computing involves more than just cellular (mobile) systems and fact may be leveraged by WiFi, WiMAX, and other forms of wireless as well as wired networks.
While MEC is helpful for LTE, and absolutely necessary for some 5G applications, it brings with is new security concerns. Minimally, edge is another point of potential cyberattack by bad actors, and generally speaking, another node for telecom operations to manage physical security. Like centralized resources, the edge needs software to prevent hacking, malware, and denial of service attacks. By its very nature, however, the edge represents many distributed nodes throughout the network, which will cause difficulty in keeping software updated.
There are many potential use cases for AI within the cybersecurity domain. For example, AI may be used in IoT to bolster security, safeguard assets, and reduce fraud. There are varying opinions about security in IoT. For example, some companies favor a distributed (decentralized) approach whereas other companies believe a more centralized approach leveraging strictly centralized cloud architecture makes more sense.
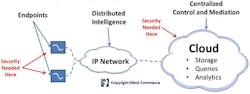
Computing at the edge of IT and communications networks will require a different kind of intelligence. AI will be required for both security (data and infrastructure) as well as to optimize the flow of information in the form of streaming data and the ability to optimize decision-making via real-time data analytics. (See Figure 3.)
Figure 3. Edge Computing Architecture
AI has various advantages including the fact that is a more lightweight application (because it does not require all the data that comes with tracking digital signatures/code for known viruses), more effective in identifying malware, easier and less costly to maintain as there is no need to constantly identify new malware code. This is all because AI-based security is looking for malicious behaviors rather than known malicious code.
Think Beyond Traditional Security
AI-based security assesses behaviors rather than scripts, such as determining what the likely outcome would be of allowing data access and/or requests for control that would potentially impact the overall system in a harmful manner. AI-based security will be required as edge computing systems are inherently resource constrained (compared to centralized computing systems) including storage. This means that there could be an issue with storing large malware signature files. More likely, the biggest issue would be the desire to not bog down distributed computing systems with frequent security updates associated with traditional cybersecurity (e.g., updating the signature files for new threats).
As edge computing grows in importance, so will the market to protect edge nodes, data, and access to networks. Accordingly, the total global cybersecurity associated with edge networks and equipment will reach nearly $72B USD by 2024.
Rather than concentrate solely upon traditional forms of cybersecurity, risk management is a more comprehensive approach, taking into account security, privacy, and decision-making.
The beauty and the curse of AI is that it will act autonomously. However, the type of autonomic action that AI takes will not always be in the best interest of the individual. Stated differently, AI may help automate things, make things faster, more efficient, and more effective, but the question remains: At what cost? It may be in the collective best interest of society for AI to place priority upon preserving the life of students in a school bus, but it may be at the expense of an individual riding a motorcycle.
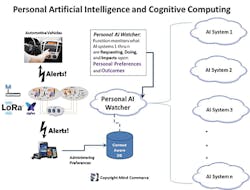
One of the things that Mind Commerce has advocated at the personal/individual level is a Personal AI, which represents software, platform, and/or systems (etc.) that are under complete control of the individual. This Personal AI would act as a form of AI Mediator, providing checks and balances against autonomous AI, which may be embedded in many unseen systems and processes. (See Figure 4.)
Figure 4. Personal Artificial Intelligence and Cognitive Computing
AI is undergoing a transformation from silo implementations to a utility function across many industry verticals as a form of general purpose AI capability. This capability is becoming embedded and/or associated with many applications, services, products, and solutions. Mind Commerce sees AI innovation in a variety of areas including personalized AI to both support and protect end users.
AI is both a blessing and a curse, leading to concerns about false positives with autonomous decisions
AI has the potential to directly and/or indirectly cause manifold adverse impacts on both humans and things (e.g., IoT). Therefore, creation of a virtual safety net will be crucial in future AI systems, especially with general purpose artificial intelligence. The concern is that AI will cause unintended consequences that could be mitigated with an AI Watcher function as part of Personal AI.
More to Come
Mind Commerce sees the AI segment as currently very fragmented, characterized with most companies focusing on a silo approaches to solutions. Accordingly, there is a need to take a more integrated approach with general purpose AI and a view towards risk mitigation as a whole rather than merely focus on traditional cybersecurity.
[toggle title=”Personal AI Watcher?” load=”hide”]Mind Commerce also sees integration of the Personal AI Watcher function within many consumer products and services. For example, the below diagram depicts use of the Personal AI Watcher function within a Connected Vehicle.
Integration with person motor vehicles is only one example of how the Personal AI Watcher function will integrate into everyday life. There are many other areas in which AI will both serve and protect from both other AI functions.
[/toggle]
Like this Article?
Subscribe to ISE magazine and start receiving your FREE monthly copy today!
For more information about these areas, we encourage readers to visit the ISE Research page at https://isemag.com/research/ where visitors will find reports such as Cybersecurity Market by Segment (Consumer, Enterprise, Industrial, and Government), Use Case and Solution Type, Industry Verticals, and Regions 2019 – 2024, as well as more information about ISE custom research services.
References and Notes
"S.734 – Internet of Things Cybersecurity Improvement Act of 2019" Congress.gov. 116th Congress (2019-2020). https://www.congress.gov/bill/116th-congress/senate-bill/734/
"TR246 Fraud Survey Report 2019 R19.0.1" TMForum. https://www.tmforum.org/resources/technical-report/tr246-fraud-survey-report-2019-r19-0-0/
"5G security: ‘5G networks contain security flaws from day one’". 5G Gradar. By Jimmy Jones 2019-11-25T21:32:16Z. https://www.5gradar.com/features/5g-security-5g-networks-contain-security-flaws-from-day-one